If you CreateProcess then IMMEDIATELY NtSuspendProcess, the process is created then suspended while not even fully initialised (only its image and NTDLL.DLL are loaded and in the module list).
It is also not appearing in the task manager process lists, neither in the Processes tab, nor in the Details tab.
It does appear in Process Hacker (non-admin, without its kernel driver) so the process can still be found from other user-mode processes, but it’s interesting that task manager doesn’t list it.
Using Process32First and Process32Next to enumerate all the processes as recommended by Microsoft does show the process, so it’s certainly the way the task manager itself lists the processes that is faulty, not the API functions themselves.
Might be useful to hide a process from the default task manager, or to investigate further to know more about the cause of that oddity?
I don’t think I’ll follow the white rabbit on that one any time soon though.
Author: Pierre CIHOLAS
Force a program to run without administrator privileges, as current user (Windows)
Same the following script into a .bat file:
cmd /min /C "set __COMPAT_LAYER=RUNASINVOKER && start "" %1"
You can now drag and drop your executable on that .bat file to force it to run as current user.
Found on SuperUser with other solutions, if you are interested.
How to get started in video game hacking?
Certainly the most asked question in game hacking communities: “How to get started?”
There are many thing to say about that, so I have decided to write my own answer in a dedicated article so I can just paste a link to people asking, and so I can improve it periodically to get an answer as complete as possible.
This article is obviously only my own opinion only, there is more than one way to get started or to learn everything that is required.
However, in this method and oppositely to the majority of others, I took into account the level of motivation, and have done everything possible to keep video game hacking exciting and fun.
This article is aimed especially at beginners or absolute beginners (even not knowing how to code), if you have already a little experience you might find some valuable advice here and there, and finally if you are an experienced reader, please let me know your opinion on my method and any suggestions to improve or complete it.
Having the right mindset
Know what you are willing to do
People start learning game hacking with various objectives and are willing to devote themselves to different extent.
Some want to learn to make their own private hacks bypassing anti-cheat defences and are willing to dedicate significant time for it while others want a hack that works right away and are not willing to devote more than a few hours having something working.
There is no shame in not being willing to spend time or energy in anything, you simply have to acknowledge it and be realistic on what’s beyond your reach consequently.
If you want a hack for that one game that has very basic protection and are willing to spend just 2 hours maximum, then you’ll want to look for a compiled ready to be executed or injected hack available in a hacking community forum.
If you want to make your own private cheat with private anti-cheat bypass and are willing to spend a few hours every week for the next few months, then yes, you definitely can get it.
However if you are willing to give 4 hours maximum and you want a private undetectable cheat, then you have to be realistic and accept that this is simply not possible.
And if you think of buying so-called “private” cheat from shady seller, beware the scams, and not only the ones in which you are given an old, detected and public cheat, but also the ones in which they just take the money before giving you the finger.
Simply be clear on what you want accordingly to what you are willing to invest.

Be ready to learn
Ideally, you should start video game hacking by being willing to learn, and if you start from really zero, be willing to learn a lot.
More than being willing to learn, that should be the main goal, video game hacking should just be a pretext to learn, not the final objective.
This means that if you want to do advanced things, such as hacking competitive anti-cheat protected games, it will take some time and commitment.
This doesn’t mean that it won’t be fun and exciting from the get go, on the contrary, I am going to present you a method in which you will be hacking straightaway, with no prior knowledge required.
Simply keep in mind that learning takes some time, and it’s not always easy, especially when learning autonomously as you will probably be, however I guarantee that you will quickly surprise yourself when you will understand new principles and master new skills.
And isn’t it good to feel intelligent? 🙂 I know it, it happened to me, it was a Thursday if I remember correctly. 😀

Learn game hacking, not just to hack only that one game
Many people start their video game hacking adventure by registering on a hacking community and this is indeed a good thing, it is good to mangle with people sharing your interest, especially for such an activity that is often frowned upon.
Unfortunately many of them start game hacking with one clear objective: To hack that one competitive anti-cheat protected game they currently play and no other.
Well, if you start video game hacking from zero, let’s be clear:
You won’t be hacking anti-cheat protected games tonight, not tomorrow either, but in a few weeks at the very least.
If that is your case, refrain from being single minded on which game you want to hack, and be open to the possibility of starting first by hacking other game that are unprotected or less protected than the game you wish to hack.
This is really important, otherwise the challenge will be too hard, you will fail repeatedly, get frustrated and finally abandon without getting anything from this adventure.
Handling challenges wisely
In the process of learning (anything, not only game hacking), nothing destroys motivation and enjoyment more than failing over and over again.
For that reason, it is important to know what is beyond reach and what is simply too complex with your current experience and knowledge.
That does not mean that there are things that you cannot do, but for these things you should be aware that they are too complex and consequently subdivide the final goal into smaller easier achievable individual challenges so that you will go step by step, repeatedly succeeding, one small challenge after another, gaining experience to then achieve your final objective.
This is a bit similar to what we are doing when programming, we divide a complex program in smaller functions that do one specific thing at a time.
You should do the same with challenges.
“Controlling complexity is the essence of computer programming.” – Brian Kernighan
For example, let’s say that we have for goal to make a radar that will reveals the position of other enemies.
This will involve reading the memory of the game process to make sense of it.
One should ask themselves “Do I know how to read another process’ memory?”.
If the answer is no, then the final goal is currently out of reach because we currently lack a skill required to achieve it.
Therefore, it should be subdivided into a first smaller challenge: Reading another process’ memory (I will write a set of exercises to learn these basics).
For these smaller challenges, forget about the game entirely, step back a little and make yourself an exercise such as coding a program that loads things in memory showing the memory address where it is stored and another program that will reads the data.
Then only once really comfortable at reading other process’ memory move on to the next task.
And by “being really comfortable” I don’t mean having done it once, I mean truly understanding what you do and how it works, in other words: Build STRONG knowledge.
Be mindful of your capacities, do not underestimate any task, choose your challenges wisely, subdivide them to keep them achievable, process one thing at a time and do not skip any steps.
This way your adventure will be made of numerous small successes and it will be frustration-free.
Everybody has struggled at the beginning
In your adventure, you will try many new things, and now and then, you’ll bump into a problem.
Sometimes, it just won’t work, and you won’t find why, it will feel like it doesn’t make any sense, and you might doubt your knowledge, your skill, or even your general intelligence.
This happened to me many times when I was learning programming, and some times I almost considered having myself checked for autism.
Boy, did I struggle…
I have spent hours finding the reason of a bug that was in fact very silly, like a wrong variable type that was right under my nose during all this time.
Making small programs seemed to take me a lot of time, and I thought that I was just straight bad at it.
This is also amplified by the fact that when you read code, you read finished, polished code, and you don’t see the hours of research, write up and debugging that were done.
Moreover, there is this myth of some people so good at programming they can write perfect bug-free programs as fast as we, normal people, write text.
A good example is the Youtube channel ZeroMemory that I recommend, have a quick look at one of his videos:
The setup is perfect: lines of code, intriguing electronic music with Matrix-y vibes, you feel like a hacker just by watching.
And look at that! It really feels like this guy just hits record and writes hacks live.
Well, let me cut the bullshit:
There is NO genius programmer.
Behind this code there are hours of research, attempts, fails, and general trial and error.
At the beginning when I thought I wasn’t good at coding, I thought that out there there were guys who could almost just roll their heads on the keyboard and make perfect programs.
I thought it was just me that was having a hard time understanding how some functions work, how to design and organise my code, and all those basic things.
My background is purely oriented towards network security, but I started working more and more with academically trained and experienced professional programmers and guess what?
All of them have struggled, all of them have spent hours solving obvious silly bugs, all of them have made mistakes and all of them still do.
And if you don’t believe me, I recommend you the following presentation by Brian Fitzpatrick and Ben Collins-Sussman, programmers working at Google named “The myth of the genius programmer”
In short, be assured that you are just as capable as anybody else, a bit of struggle will be here and there, it is part of the journey, and it’s absolutely normal.
What you do has real value
You might just want to hack games for fun, but the techniques involved in this discipline are real skills that have real-world value.
Learning a programming language or getting more experience with it, understanding concepts of computer science, reverse engineering, and many others are widely demanded skills in the industry and the job market.
If you doubt it, check on LinkedIn all the people putting on their CV their computing skills, the programming languages they know, etc…
Or you can also check out all the universities, schools and training centres offering expensive courses to learn all this.
And even if you are not in working in IT, programming and computers allow you to do so many different things for so many different purposes that I doubt that learning these skills would be useless for anyone.
It might seem like you are just hacking games alone in your home only wearing undies, but you are in fact learning highly valuable skills that some other people pay the high price for in education.
In other words: By learning game hacking you are not wasting your time, quite the contrary.
Okay now that we are in the right mindset, let’s dive into the practicalities.
Learning game hacking (and staying motivated)
Most people would tell beginners that the very first thing to do is to learn a programming language suitable for video game hacking, such as C++ or C#.
This is good thinking, and this is true, very quickly to do advanced hacking you will need to code, but I don’t think it is a good idea for an absolute beginner to start head down with learning programming only.
It’s not a good idea for one reason:
Learning a first programming language from zero is very demanding, time consuming, challenging, and you don’t get rewarded very fast for your efforts.
What I mean by that, is that someone who goes learning a programming language to hack games will not start any actual hacking until many, many hours spent learning the language.
This can make learning the language perceived as an unwanted tedious task, and something as fun as video game hacking can transform into an excruciating soul-crushing activity.
Let’s admit it, when one wants to learn video game hacking they want to start hacking straightaway.
I myself did want to start RIGHT NOW.

Learning a programming language, especially learning the first one will take several dozens of hours at least during which you will be doing things not quite related to game hacking.
This means that the ratio of efforts/fun will drop into too much efforts and it is very likely that you will give up along the way.
So where to start if not by learning a programming language?
In my opinion the best option would be to start learning how to use the basic game hacking tools like Cheat Engine (or preferably the less known but at least as capable CrySearch, open source as well and amazing well written by Gijs Rijnders), ReClass (open source as well), and many others.
This way we straightaway dive into the matter of interest, and these tools are simply amazing, with almost no prior knowledge or experience in game hacking or even general computing, you can already start doing fun stuff in a matters of hours if not minutes, like getting invincibility, unlimited bullets, teleportation, etc… (obviously, starting with unprotected games, I’m sure you have an old game you wished you could cheat in, even emulated console games work, otherwise I’ll suggest you a game to experiment on further down this article)
For that reason, I recommend the awesome book “Game Hacking – Developping Autonomous Bots for Online Games” by Nick Cano.

This book is extremely practical, not even 10 pages in you’ll already be at your computer doing actual game hacking.
Keeping one motivated is an important factor to define success (it is my opinion THE most important) and by diving straight in like that, the motivation will only increase, because you are going to prove yourself that they can do it, that it’s not black magic, that it’s actually simpler than it looks like, and that the possibilities are simply overwhelming – and overwhelmingly exciting.
Proving yourself that you can do something new is a very good feeling, the motivation skyrockets, the possibilities multiply and the amount of devotion you are willing to put into learning more goes always higher and higher.
Now is the time to make good use of this extra kick of motivation, now is the good time to start learning a programming language.
You don’t need to finish reading this book or learn everything about game hacking software first before starting learning a programming language, on the contrary I think the best thing is to learn those 2 things in parallel.
Learning practical game hacking with tools and hands-on exercises will keep the motivation high, and you can then straightaway spend this motivation in reading an extra chapter on the programming language of their choice.
I will not detail too much which programming languages are suitable for video game hacking in this article, however since “Which programming language should I learn?” is one of the most repetitively asked question, it deserves a paragraph, for the sake of clarity.
In short you want a programming language efficient (little abstraction and overhead), where you have fine control of your program, its memory and its execution, you will want to be able to call Windows API functions and use some useful libraries.
The most dominant programming languages for game hacking are nowadays C/C++ and C#.
Others can do the job, but fewer people make the choice to use them, therefore you might get more support in the hacking communities by choosing one of these 3, and if you learn them you will be able to use easily sources written in those languages, which are the majority of the sources we find nowadays.
If you don’t know what to choose and want my personal opinion, I highly recommend you to learn C++ for video game hacking (or even general hacking).
Another question that comes around many, many times is where to start learning a programming language.
If you intent to learn C++ then I would suggest the amazing website www.learncpp.com
Straightaway you will arrive on the table of content and can click the first chapter to get started, otherwise there are many other books and websites available.
Try not to spend too much time choosing where to learn, whether a book or website, just pick one with good reputation or reviews and you’re good to go.
Keep in mind that all the time you spent hesitating is simply wasted.
In short: Stop hesitating, just start learning, it doesn’t really matter from what or where.
Now as you can deduce from the table of content on their website, learning C++ is long, and for any absolute beginner that was advised to start game hacking by learning this language this is simply going to crush their motivation.
As an absolute beginner eager to start hacking, seeing this table of content (that is not even half complete on this image) and realising how much work is ahead only means that they will have to first commit to dozens of hours of tedious autonomous learning on something that’s not exactly what they really want to do.
Therefore, try to be mindful of your motivation and energy levels and if you feel that the excitement is going down, bump it up by doing hands-on and fun experiments.
At the end of this first phase of learning you will know how to make programs and how to reverse engineer games to hack them.
If you intent to make a cheat with overlay (for example an ESP), I strongly advice you to make a first one on an unprotected game to train yourself without having to worry about possible defences that could cause you trouble.
Many free games are available for that, just pick one of the same genre of the game you want to make a cheat for (if you want an ESP for a FPS, use an unprotected FPS).
If you don’t want to search and choose and want my recommendation (for FPS), I recommend you to use Assault Cube because it is free, open source, it has bots so you can do your shady things locally without bothering anyone, many other hackers have experimented with it so you can read other cheats for your research and it allow you to develop most of the basic cheat functions (ESP, unlimited health, unlimited ammo, teleportation, no-clip, etc…).
You’ll then be ready to attack the only thing that stands in your way to hack competitive online anti-cheat protected games: Bypassing anti-cheats defences.
Anti-Cheat bypassing
This is by far my favourite activity, because it is in fact straight up hacking.
I spend most of my time doing stuff related to it.
So much that to be honest I neglected a bit my reversing skills, but I’m working on that right now.
Bypassing an anti-cheat consist in outsmarting their solution.
This is really exciting because there is this feeling of adversity: Some skilled security guys have made a defence system and you have to find a way around it.
It’s a cat and mouse game: hackers find bypass methods, at the beginning they are private, then they spread to the public, the anti-cheat either blocks or detect them, and the next round starts.
Therefore you will not find long term undetected bypass methods ready off the shelf because they would get fixed, or if you do find public bypasses you are likely to get banned when using them.
That doesn’t mean that everything related to anti-cheat bypassing is either kept private or detected, many bypasses exploit weaknesses that are not fixable by design, by concept.
A good example is handle hijacking: Some system processes of Windows have process handles with sufficient permission to read and write other program’s memory, and some of these system processes absolutely NEED them, they cannot be removed or altered without creating instability in the system or even crashes. (if you do not know what a process handle is, consider it just as an authorisation given by the system to do operations on processes)
Therefore this method cannot be completely fixed, therefore anti-cheat have instead started analysing the processes having those handles looking for suspicious activity since hackers could make these processes do operations on their behalf.
Public bypasses using this method will most likely be detected, but if you can be stealthy enough, you can still use it.
So where to start then?
A very good starting point is to read sources of public bypasses and understand how they operate, even if the bypass itself is detected understanding the techniques involved will be very valuable.
If you want to go (too) fast, you can take the risk to modify a public method, increasing its stealth hoping to remain undetected.
However, even if you decide to do that instead of writing your own bypass, I encourage you to get the required knowledge to assess your bypass and understand it fully.
Anti-cheat bypassing require to have a sharp knowledge of the system internals (since the large majority of games run on Windows, I’ll just talk about Windows here, but the principle applies to other OSes).
Therefore, I suggest that you start reading 2 books in parallel:
Practical Malware Analysis – The hands-on guide to dissecting malicious software and Windows Internals (7th or 6th edition, you want this book to be as recent as possible considering that Windows is constantly evolving)
An alternative to Practical Malware Analysis is The Malware Analyst’s Cookbook, I recently bought because I intent to improve my reversing skills with it.
It has good reviews but I cannot testify of its quality myself yet.


You will want to read Practical Malware Analysis at the very least until the chapter 10.
You will learn many new skills that will help you to both reverse engineer games, anti-cheats, and windows binaries as well to take advantage of them.
The chapters past the chapter 10 are more malware oriented, however, they are extremely useful to increase the stealth of your bypass and cheats.
This first book is extremely practical and you will find a set of exercises at the end of each chapter, and the exercise will take you more time than reading the chapter.
This is a rather heavy read, or at least it was for me because I had to learn a lot every chapter, therefore I suggest that you read Windows Internals in parallel.
Windows Internals felt like a more relaxed read, it is still practical, but it brings knowledge more than it properly “trains” you oppositely to Practical Malware Analysis, therefore you can read it when you are a bit lower in energy and don’t feel like focusing a lot.
It is full of illustrated experiments that you can reproduce (and I encourage you to reproduce any experience you consider useful) and you will get a sense of how to go around defences and how to stay undetected.
With this new knowledge and experience, trust me, you will come up with several ways to bypass anti-cheats.
Keep reading sources and experiment as much as possible.
That’s pretty much it.
By the end of this adventure you will be a skilled reverse engineer, programmer, and hacker, and I am sure you will keep excellent memories of this experience.
External overlays without window
Since many people – including me – suspect windows of external overlays to be detected by anti-cheats, having an overlay system without a window entirely has excited many people in the game hacking community.
Traditional overlay windows have very specific and detectable characteristics in general, like being at least as big as the game’s client area, being WS_EX_TRANSPARENT and WS_EX_LAYERED, and sometimes WS_EX_TOPMOST, even if you can remove this one by sending back your window at the top at each cycle.
Many possibilities were considered, including leveraging “whitelisted” programs, who are authorised to draw on top of game’s frames such as FRAPS, Overwolf, Discord, NVIDIA, and many other gaming related software.
I have personally developed an Overwolf plugin that allowed me to display on top of my game’s frames, but I never finished my system, I wasn’t satisfied with it, but other people have implemented full systems, such as the plugin “Ultimate crosshair” that you can see in action here:
Anyway, I recently found a solution that lets you draw your overlay without a window entirely (technically we are still using a window, but we don’t create it and it’s not linked in any way to the program).
The solution is actually so simple that I felt like facepalming myself when I found it.
If you feel like a small challenge here is how I found it, perhaps can you find it too without reading the solution? 😉
I was using Process Hacker checking out the windows in my system (View > Windows) looking for windows that I could hijack.
I thought that if I found a window that was already taking the fullscreen, visible, layered and transparent I could just render on it.
But then an idea came to my mind, is there no other windows that are always on top and take all the screen?
Hint: There are at least 2…
Directly calling ZwReadVirtualMemory for stealth and performance
I am writing a last handle hijacking user-mode bypass and I am going way over the top to avoid detection and get performance with all sorts of tricks (e.g. using spinlocks for synchronisation instead of semaphores or other synchronisation objects to have an stealthy OS-independent inter-process synchronisation system that leaves no tracks, no handle of any sort)
I will share that soon.
I know that since anti-cheats are in kernel they have the advantage over me in user-mode, but I want to push user-mode stealth to its limits before going kernel myself, simply because I enjoy coding/hacking.
One thing bugged me:
I was calling NtReadVirtualMemory and NtWriteVirtualMemory (NtRVM and NtWVM) or the classic RPM/WPM from the process having the handle that I abuse.
Small background in case you don’t know:
When you call RPM/WPM, some wrapping operations are done to return a BOOL instead of an NTSTATUS and other things, then RPM/WPM calls NtRVM/NtWVM that then calls the kernel function ZwReadVirtualMemory or ZwWriteVirtualMemory (ZwRVM and ZwWVM)
I made a small experiment and hooked these 2 functions to detect myself and I could detect when these functions were called and retrieve their parameters which could also be done by an anti-cheat.
I do not know if they use this user-mode hook based detection technique and I do not care, as I said I just enjoy coding/hacking for its own sake.
However, certain system processes having interesting process handles have the control flow guard (CF Guard) that apparently prevents from putting simple hooks (it did prevent me from setting my hooks, but there are certainly ways to go around that, there always are).
So how can I read another process’ memory without calling these 2 functions?
My solution: Calling directly the kernel function ZwRVM or ZwWVM.
To do this I would have to replicate the operations that NtRVM does before doing the syscall that leaves user-land to kernel-land.
I thought that there will be many operations before the syscall, to check stuff around and prepare the travel to kernel-land, but then I opened ntdll with IDA and saw this:
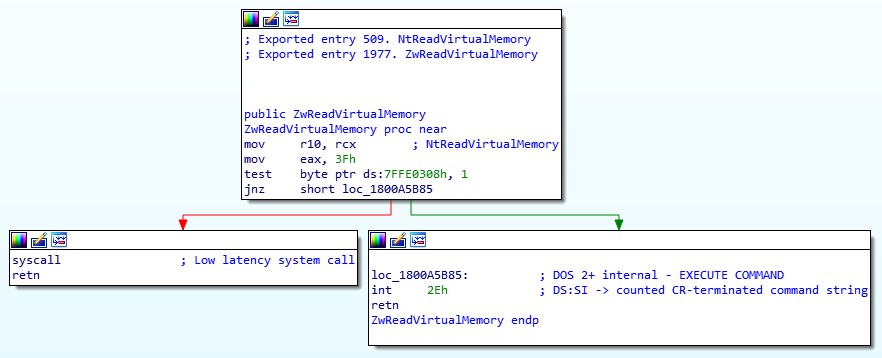
Well, that’s pretty simple …
The only difference in NtWVM is the number moved into eax.
So I fired Visual Studio, new project, add new source file “ZwRWVM.asm”, wrote this code:
- .code
- ZwRVM proc
- mov r10, rcx
- mov eax, 3Fh
- syscall
- ret
- ZwRVM endp
- ZwWVM proc
- mov r10, rcx
- mov eax, 3Ah
- syscall
- ret
- ZwWVM endp
- end
Then I did a quick program to test that:
(Click here for the GitHub repo)
- #include <Windows.h>
- #include <iostream>
- using namespace std;
- extern “C” NTSTATUS ZwRVM(HANDLE hProcess, void* lpBaseAddress, void* lpBuffer, SIZE_T nSize, SIZE_T* lpNumberOfBytesRead = NULL);
- extern “C” NTSTATUS ZwWVM(HANDLE hProcess, void* lpBaseAddress, void* lpBuffer, SIZE_T nSize, SIZE_T* lpNumberOfBytesRead = NULL);
- int main() {
- DWORD pid;
- cout << “PID: “;
- cin >> dec >> pid;
- HANDLE hProcess = OpenProcess(PROCESS_ALL_ACCESS, FALSE, pid);
- if (!hProcess)
- return EXIT_FAILURE;
- int intBuffer = 555555;
- void* lpBaseAddress = nullptr;
- SIZE_T lpNumberOfBytesRead = 0;
- cout << “Address to read: 0x”;
- cin >> hex >> lpBaseAddress;
- NTSTATUS status = ZwRVM(hProcess, lpBaseAddress, &intBuffer, sizeof(int), &lpNumberOfBytesRead);
- cout << “ZwRVM returned “ << dec << status << endl;
- cout << “intBuffer = “ << dec << intBuffer << endl;
- cout << “lpNumberOfBytesRead = “ << lpNumberOfBytesRead << endl;
- system(“pause”);
- return EXIT_SUCCESS;
- }
(When using a .asm assembly file don’t forget to right click your solution, go to Build dependencies/Build customizations, then tick “masm(.targets, .props)”)
I fired up my favourite guinee-pig program:

And successfully read its first integer:

Well, that was much simpler than I expected lol
With this solution I could obviously not detect myself anymore by hooking RPM, WPM, NtRVM, and NtWVM in the process of which I abuse the handle.
In addition this gives us the small speed boost that calling directly Nt functions gives over using RPM/WPM that I calculated in a previous experiment (about 5%, I will post this experiment on the blog soon).
Feel free to use this for extra protection.
Bonus meme!
Shellcode Exec & DLL Injection lately
My favourite book is now Intel’s x64 instruction set lol
Getting an hijacked thread execution state from the instruction pointer
When you execute some shellcode in a new thread, things are simple:
You can simply write your shellcode doing whatever you want it to do and finish it with a return.
On Windows, you execute it with CreateThread (or CreateRemoteThread from another program) then you can simply use WaitForSingleObject with the thread handle and voila.
Unfortunately with thread hijacking, this is impossible, because we interrupted a thread that was busy doing operations that we don’t know with a stack in a state that we don’t know either, which means that executing a return instruction would make the thread return to the last return address on the stack and mess up completely its operations.
We have to be clever.
I took a (brief) look around, and it seems that many people go for a solution with a byte set to a certain value to signal that the execution is complete before maintaining the thread in its current state with whatever solution.
I did not really like this solution, since it means that we have to read the target process memory, and therefore we need a process handle with enough rights to read the memory.
Instead I wanted a solution that would use only what we already have for the thread hijacking, especially the thread handle.
We can detect whether the hijacked thread has completed execution with the information that we already have:
- We can design our shellcode to enter a very small infinite loop at the end of its operations (with for example JMP REL8 -2)
- We know the address at which the shellcode starts
- We know the size of the shellcode and therefore the address at which the shellcode ends
- We can get the address at which the instruction pointer is only with our thread handle that we already needed for the thread hijacking
So we simply finish our shellcode with our bytes infinite loop (JMP REL8 -2, opcodes: 0xEB 0xFE) and in our hijacking program we simply do an infinite loop that executes GetThreadContext while the instruction pointer has not reached our infinite loop.
When this is done, we could simply re-suspend the thread, reset its context to its initial state before we hijacked it, and resume it.
I have done a proof of concept program for x64 shellcode that I pushed on GitHub if you are interested.
What happens when overwriting memory being executed?
Imagine that you have some executable memory, with for example an infinite loop using a short jump like that:
NOP
JMP REL8 0xFE (-0x2)
This generate the following shellcode:
0x90, 0xEB, 0xFE
Now, what would happen if another process or another thread was modifying the destination of the short jump?
Would it be possible that the instruction executes while the destination is BEING overwritten?
0xFE is 1111 1110 is binary.
Could it happen that this short jump sometimes jumps of 0x1E (0001 1110) because it is currently being overwritten to 0x00 and is not entirely overwritten?
Is that possible?
Note that I am interested only in knowing the possibility of an incomplete overwrite of a single byte, no more than that.
To verify that I have made a C++ program that executes a shellcode in a new thread with the infinite loop I showed above.
The main thread modifies the destination of the short jump to the furthest short jump (JMP REL8 +127).
At that address, the shellcode modify itself, restoring the destination of the JMP to -0x2 to make it an infinite loop again, then right after that there is another small shellcode that calls GetSystemTime filling a SYSTEMTIME struct before jumping back to the infinite loop.
Meanwhile, the main thread checks in a while(true) loop is the SYSTEMTIME struct has been filled, meaning that the shellcode of the other thread has executed correctly, and when it is filled, it resets it to 0 with SecureZeroMemory before restarting the operation (modifying the destination of the short jump to make the other thread get the SYSTEMTIME).
A JMP REL8 can jump from -128 to +127, and the only why it could crash is if the destination is -1 (0xFF) since it would set the next instruction to execute to 0xFF which won’t work.
Therefore, I have placed my JMP REL8 surrounded by NOPs and a single 0xCC (breakpoint) at the end.
This means that if at any moment the destination is being read while incompletely overwritten, the shellcode will start executing NOPs until arriving on the breakpoint, and I will know that an incomplete destination has been read and executed.
The last case would be if the incomplete overwriting of the destination byte led to the execution of JMP REL8 0xFF (-1) which would place the instruction pointer on 0xFF and it would crash because it is not a valid opcode just by itself.
I have ran my program for about an hour and it never crashed or hit a breakpoint, therefore, I think that this is not possible.
If someone can confirm, or better has the explanation of why this cannot happen, this would be much appreciated.
The code of this program can be found on my GitHub feel free to experiment with it.
Why does it matter?
Thread hijacking is rather straightforward: you suspend a thread, save its context, set its context to execute your shellcode, resume the thread and wait for it to finished executing.
You can be acknowledged of its completion for example by ending your thread with an infinite loop and reading a value in memory with ReadProcessMemory that your shellcode updated to let know your other hijacking process that it is done, or you can check if the instruction pointer is now in the instructions of the infinite loop.
Once you know that the thread completed, you can once again suspend the thread, set its context to the initial context and resume so it can go back doing whatever it was doing before.
Granted that you have correctly cleared after your operations, there won’t be any problem.
Now, this is okay for one-time execution, but if you want to execute stuff several thousands of time per seconds all these operations will slow you down quite a lot.
Instead, granted that your target process has a thread that you can hijack permanently without problem, you could use this system for the thread control, avoiding entirely to suspend, resume and change the thread context.
The thread stays in its infinite loop, you update your shellcode, then change the single byte of the destination of the jump to release the execution from the loop, the shellcode resets the destination to -0x2, execute your operations, and goes back to the infinite loop.
I am going to try that in action in a new bypass, I’ll keep you updated.
NotAnOverlay: A perhaps acceptable alternative to overlays
In video game hacking, being able to write and draw on top of the game’s frames allows uncountable ways to get new advantages, especially for ESP cheat (Extra Sensorial Perception) in which you can draw coloured boxes around players with their names, distance, weapons, health points and more, giving you an almost perfect situational awareness.
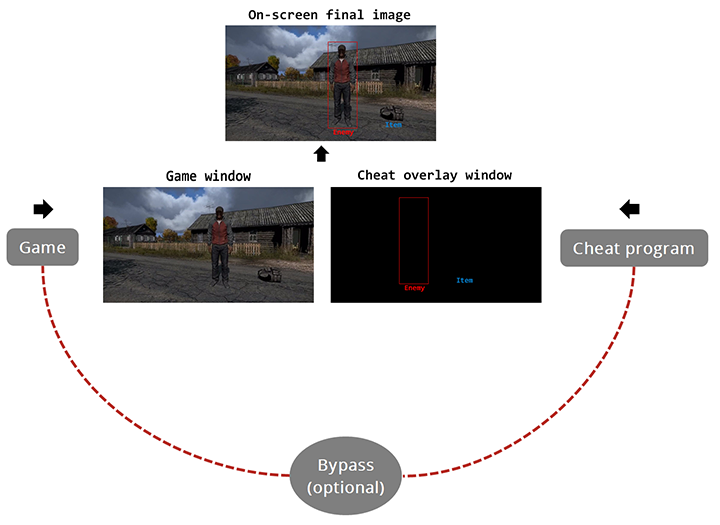
External cheats (external meaning that they run in a separate process) often use a straightforward system: creating a completely transparent window, without borders or menus, that stay always on top of others, with the same size as the game and at the same position.
This way one can simply draw whatever in this transparent window and for the user it will appear as if it is draw on top of the game’s frames themselves.
Here is how it’s done:
Whether the overlays are detected or not has been an on-going controversial topic for a long time.
In my opinion overlays are detected, but one need to understand something, having one detected element in a cheat doesn’t mean that the whole cheat will be detected.
Imagine that the anti-cheat finds a window, same size and position of the game, transparent, always on top, etc… that’s suspicious right? But okay, some unknown application might do that, banning people on that only basis might lead to false positives and ruin the reputation of both the anti-cheat and the game.
Now let’s say that in addition to this suspicious window, the anti-cheat takes a look at the process owning this window with a simple call of GetWindowThreadProcessId and by taking a look at the system handles of this process, they notice that it has a process handle to the game with full access, despite the fact that the anti-cheat driver has callbacks that prevent this from happening.
Now it is beyond a simple oddity.
They could even make sure automatically that the handle is being used for cheating purposes by analysing what this process does, for example monitoring if it is running calls to ReadProcessMemory using the handle to the game frenetically, for example by placing hooks or with other methods.
Anyway, whatever is your opinion on this, I think we can all agree that doing without such a suspicious overlay window would be a good thing.
There has been interesting approaches, like for example leveraging applications whitelisted by anti-cheats having the approval to draw on top of game frames, such as Discord, FRAPS, TeamSpeak, NVIDIA, and many other gaming related software.
Another interesting approach is to use Direct Kernel Object Manipulation (DKOM) to remove all tracks of that window, making it impossible to find with common API functions.
I have started an Overwolf plugin but haven’t finished and I do not know if I will work again on that, but if I do, I’ll share that.
I thought a bit about other possible solutions to do without an overlay window.
An idea that come to most people’s mind is to do a 2D radar to locate enemies around, but let’s admit it: Once you have tasted a state of the art ESP with overlay, there’s not going back, I wouldn’t settle for less.
So I was looking for a way to have an overlay, but without overlay window.
Then I had an idea: Duplicating the game’s image in a window (classic, custom size, non-transparent, non-always-on-top, etc… to be undetectable because like any other window) and drawing the cheat overlay on top of that image.
I wanted it to be (1) efficient, it has to run smoothly, and (2) compatible with the classic overlay systems (some people use DirectX, others use OpenGL, GDI, and probably many others).
One way to allow this would be to have the frame of the game being the background of the window, then the rendered image of the cheat overlay would just be added on top of that.
To do that I used GDI functions, the main ones being GetDC, CreateCompatibleDC, CreateCompatibleBitmap, BitBlt, and StretchBlt.
I read several times that GDI was not very performent, so I was expecting something laggy, but in fact it runs absolutely smooth!
With DayZ Standalone it ran at about 160 FPS constant as you can see in the following video:
It actually runs so smoothly that one can play by watching only the duplicated frame in the overlay window without problem.
I do not know if I will use this, but at least I know that this is definitely a viable solution.
If you are interested, I uploaded this small program to GitHub, don’t hesitate to try stuff with it.
Running a script from different IPs (using Tails & TOR)
Some months ago I had to get information on several thousands IPs. To get this information I had to use some sort of advanced WHOIS that gathers more information than classic WHOIS, including contact’s phone numbers, email addresses and more. One problem though: They were selling access to their API for some hundred dollars per 1000 queries but they gave 50 free queries per IP to try their service. I decided to find a way to run a script capable of changing IP address when the limit would be reached.
To do so, I decided to use TAILS (The Amnesic Incognito Live System) that allows natively to send all traffic, including from programs ran in the console, through the TOR network (The Onion Router). The only small challenge was to find a way to make the TOR client regenerate an IP in a script. I did not went the subtle way, I simply send a hang up signal to tor which restarts it with.
killall -HUP tor
Nothing new or groundbreaking but that was practical and efficient, I post it in case anyone is looking for it.




